Secure Your Future
Take charge of your cybersecurity with Corgevity’s solutions. Ensure your organization not only survives but thrives in the ever-evolving digital landscape.
Our Clients
Discover Our Capabilities
Unleash the power of Corgevity’s expertise. Dive into our comprehensive capabilities and fortify your digital foundation with confidence.
Consultation
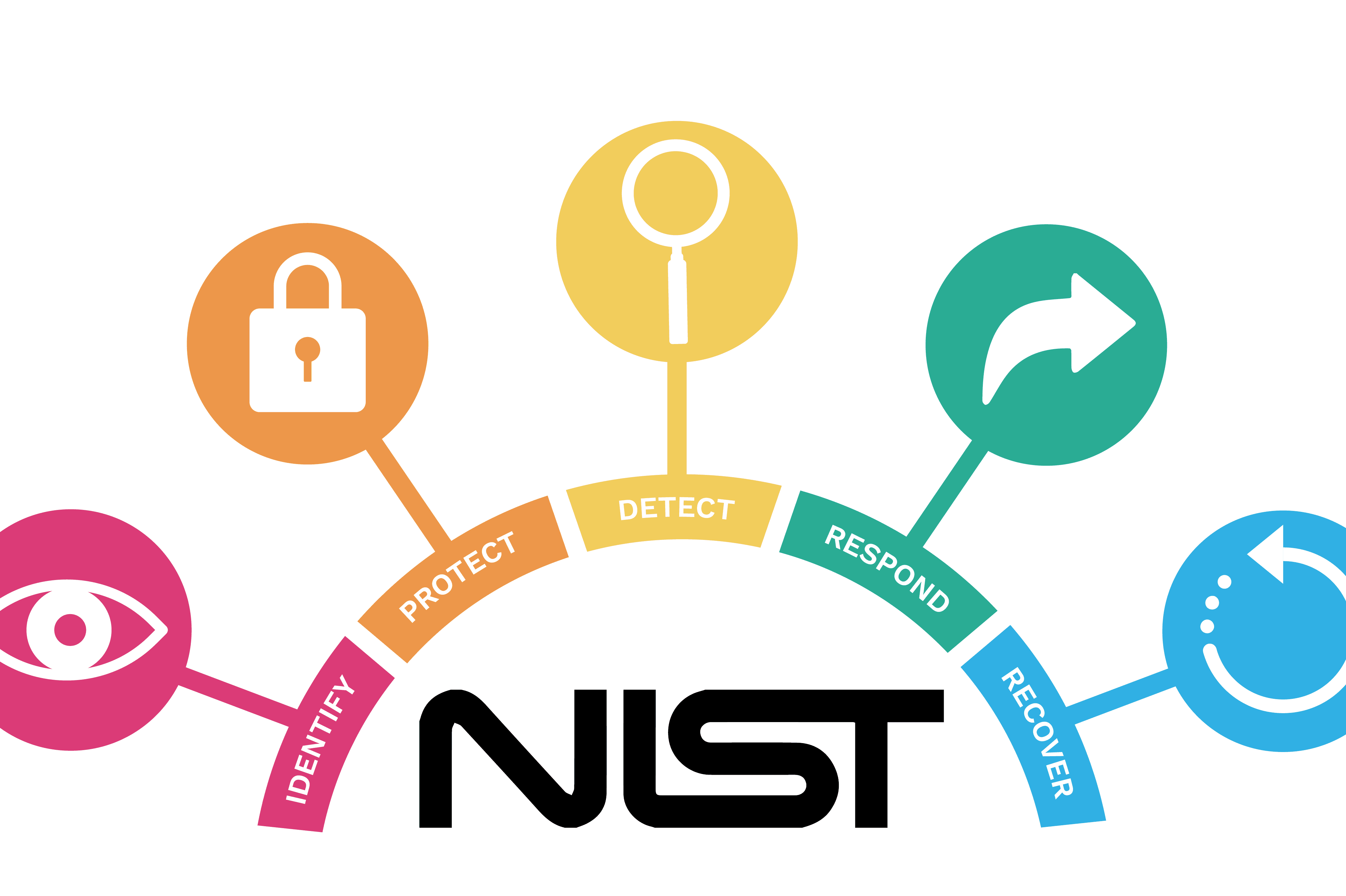
Prepare for CMMC 2.0
Ready for future government contracts? CMMC 2.0 safeguards your business from cyber threats. Let Corgevity map your NIST 800-171r2 progress to CMMC 2.0.
- Comprehensive Mapping
- Contract Readiness
- Tailored Solutions
- Thwart Cyber Threats
- Expert Guidance
- Strategic Roadmap
Stay Compliant
Regular updates to keep you compliant.
Risk Mitigation
Stay resilient against evolving cyber threats.
Streamlined Certification
Ensure a smooth compliance experience.
Risk Insights
Understand Vulnerabilities
Compliance Check
Align Security with Regulations
Powerful Insights
Perform a Cybersecurity Gap Analysis
Take control of your security. Our cybersecurity gap analysis pinpoints weaknesses in your network, ensuring effective controls and moving you closer to compliance.
- Pinpoint Weaknesses
- Enhance Controls
- Compliance Alignment
- Tailored Analysis
- Proactive Security
- Actionable Insights
Proactive Defense
Penetration Test Your Critical Resources
Vulnerability scans identify potential weaknesses, while penetration tests gauge how well your systems withstand real-world attacks. Act now to fortify your assets.
- Real-World Simulation
- ID Weak Points
- Strategic Fortification
- Security Stress Test
- Proactive Defense
- Data-Driven Security
Threat Simulation
Uncover Vulnerabilities
Defense Insights
Understand Posture
Proactive Mgmt
Stay Ahead of Threats
Response Prep
Identify Strategies
Explore More Capabilities
Delve the depth of Corgevity’s expertise. Uncover a spectrum of capabilities designed to fortify your digital foundation.
System Security Plan (SSP) Preparation
Prepare for the future with meticulously crafted System Security Plans, ensuring your systems are fortified against evolving cybersecurity challenges.
Plan of Action and Milestones (POA&M)
Navigate your cybersecurity journey seamlessly with a strategic roadmap. Our POA&M services guide you towards compliance milestones and enhanced security.
Supplier Performance Risk System (SPRS)
Mitigate supplier-related risks effectively. Our SPRS services assess and manage the performance and security risks associated with your supply chain.
Information Security Policy Creation
Establish a robust foundation for cybersecurity. Our experts assist in creating comprehensive information security policies to safeguard your organization’s assets.
Information Technology Security Training
Empower your team with knowledge. Our customized training programs ensure your staff is well-equipped to tackle the dynamic cybersecurity landscape.
Process Auditing Compliance
Ensure adherence to cybersecurity standards. Our auditing services meticulously evaluate your business processes, providing valuable insights to enhance your security posture.
Service Tiers
Choose Your Level of Service
Straight forward service tiers for organizations and businesses of any size.
Discovery
- Employee Cybersecurity Training
- Identify and Prioritize Critical Assets
- Baseline Security Policy Creation
Enterprise
- Implementation of Auditing System
- Monthly Audit Reports
- Daily CVE and Zero-day Threat Report
- Policy Creation and Review
Galaxy
- Everything Within Discovery
- Everything Within Enterprise
- Expedited/Priority Support
Begin Your Journey
Fortify your digital defenses and propel your cyber success
Our customizable approach empowers you to fortify defenses, automate cybersecurity tasks, and prioritize what truly matters in your digital landscape.

Blog
Latest Updates
-
Common Attack Vectors
SQL Injection Structured Query Language (SQL) injection is a common method of taking advantage of websites that depend on databases to serve their users.…
-
Penetration Testing Phases
Phase 1: Pre-Engagement Preparing and planning which tools and scripts to use. Agreeing to what type of testing will occur (White, Black, or Gray…
Ready to take the next step?
Cybersecurity is made easy with expert analysis and consultation. Get started today!
CMMC 2.0 Preparation
IT Security Training
Security Gap Analysis
Auditing Compliance
Penetration Testing
SPRS Analysis
SSP Preparation
POA&M Creation
IS Policy Creation
CMMC 2.0 Preparation
IT Security Training
Security Gap Analysis
Auditing Compliance
Penetration Testing
SPRS Analysis
SSP Preparation
POA&M Creation
IS Policy Creation
CMMC 2.0 Preparation
IT Security Training
Security Gap Analysis
Auditing Compliance
Penetration Testing
SPRS Analysis
SSP Preparation
POA&M Creation
IS Policy Creation