Category: Vulnerability Management
-

Understanding Red & Blue Teams
How secure are you? Let Blue and Red teams establish a robust system for your organization. What is a blue team? A blue team consists of security professionals with an inside-out view of their organization. Their task is to protect the organization’s critical assets against any threat. They are well aware of the business objectives and…
-
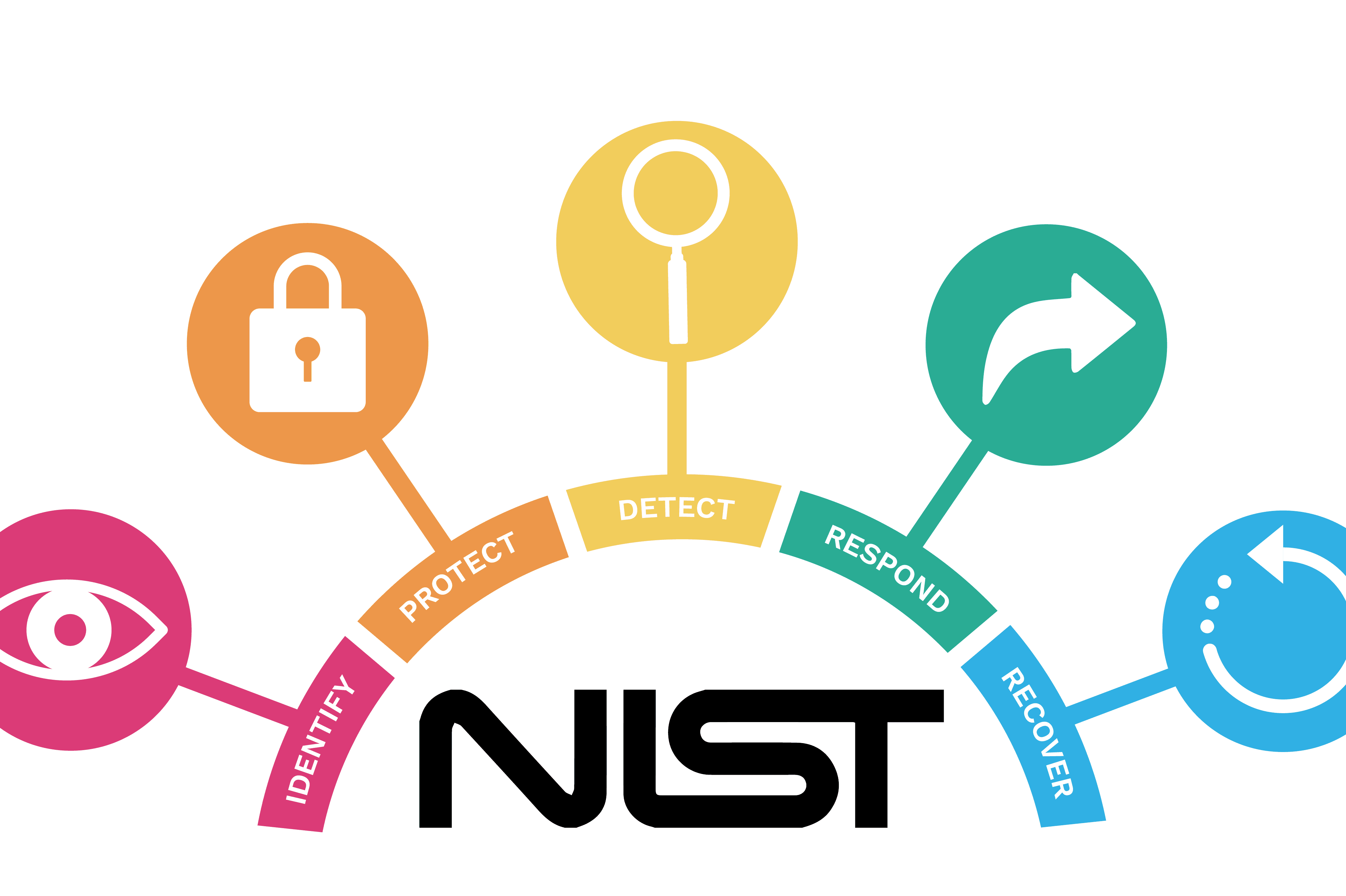
NIST Preparation
Why is NIST Mandatory? NIST preparation typically refers to the process of preparing for a security assessment or audit based on the guidelines and requirements outlined by the National Institute of Standards and Technology (NIST). Does your company’s government contracts cite the DFARS cybersecurity controls? The National Institute of Standards and Technology (NIST) SP 800-171…
-

What to Know About CMMC 2.0
The Cybersecurity Maturity Model Certification (CMMC) The Department of Defense (DOD) believes that security is a foundational aspect of all purchase decisions and should not be sacrificed for cost, schedule, or performance. The first version of the Cybersecurity Maturity Model Certification (CMMC) program was released in 2020. Its original purpose is to be a verification…
